Researchers warn of new technique bypassing traditional security scans
Cybersecurity researchers have uncovered a novel method of hiding malware inside Ethereum smart contracts, marking a new chapter in the evolution of software supply chain attacks.
Experts at digital asset compliance firm ReversingLabs identified two malicious Node Package Manager (NPM) libraries — colortoolsv2 and mimelib2 — that used Ethereum contracts to conceal dangerous URLs. Published in July, the packages posed as legitimate JavaScript tools while secretly functioning as malware loaders.
“These packages employed a novel and creative technique for loading malware on compromised devices — smart contracts for the Ethereum blockchain,” explained researcher Lucija Valentić.
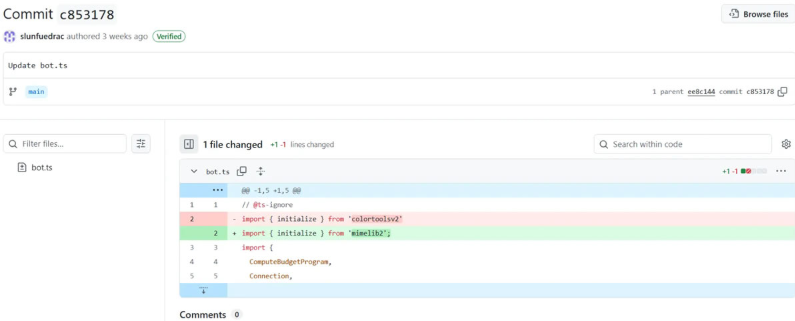
How the attack works
Instead of directly hosting malicious links, the infected packages retrieved command-and-control server addresses from Ethereum smart contracts. Once installed, the software queried the blockchain to fetch instructions and download secondary malware payloads.
Because blockchain traffic appears legitimate, this method allowed attackers to bypass conventional security scans.
Valentić added: “What is new and different is the use of Ethereum smart contracts to host the URLs where malicious commands are located. That’s something we haven’t seen previously.”
A broader social engineering campaign
Investigators also linked the malware to an elaborate deception effort on GitHub. Fake repositories, designed to resemble crypto trading bots, were filled with fabricated commits, multiple “maintainer” accounts, and professional-looking documentation to lure developers into downloading compromised code.
The approach mirrors earlier incidents involving the Lazarus Group, a North Korean-affiliated collective, but highlights how hackers are refining their evasion strategies.
The latest discovery underscores how quickly cybercriminals are adapting blockchain technology for malicious purposes. As Valentić noted, “These attacks show that repository-based threats are evolving, combining blockchain with social engineering to evade detection.”
In 2024 alone, researchers tracked 23 crypto-related malware campaigns across open-source repositories. Similar attacks have already targeted Bitcoin and Solana projects, with fake libraries stealing wallet credentials from unsuspecting developers.
Disclaimer
This content is for informational purposes only and does not constitute financial, investment, or legal advice. Cryptocurrency trading involves risk and may result in financial loss.
